IT can be thankless work. While there are lots of small problems that add up, sometimes you have a whole new software suite dropped into your lap with the expectation that you will become an expert within 24 hours. For instance, you need to implement an Identity and Access Management (IAM) platform, like OneLogin, and your boss sends you a brief email saying “let’s use SAML.” It quickly becomes your job to understand what SAML is and how to manage SAML, if that’s even a thing one does.
Okay. Take a deep breath. You’re in luck! OneLogin is pretty easy to implement once you have the correct framework. Let’s dig in.
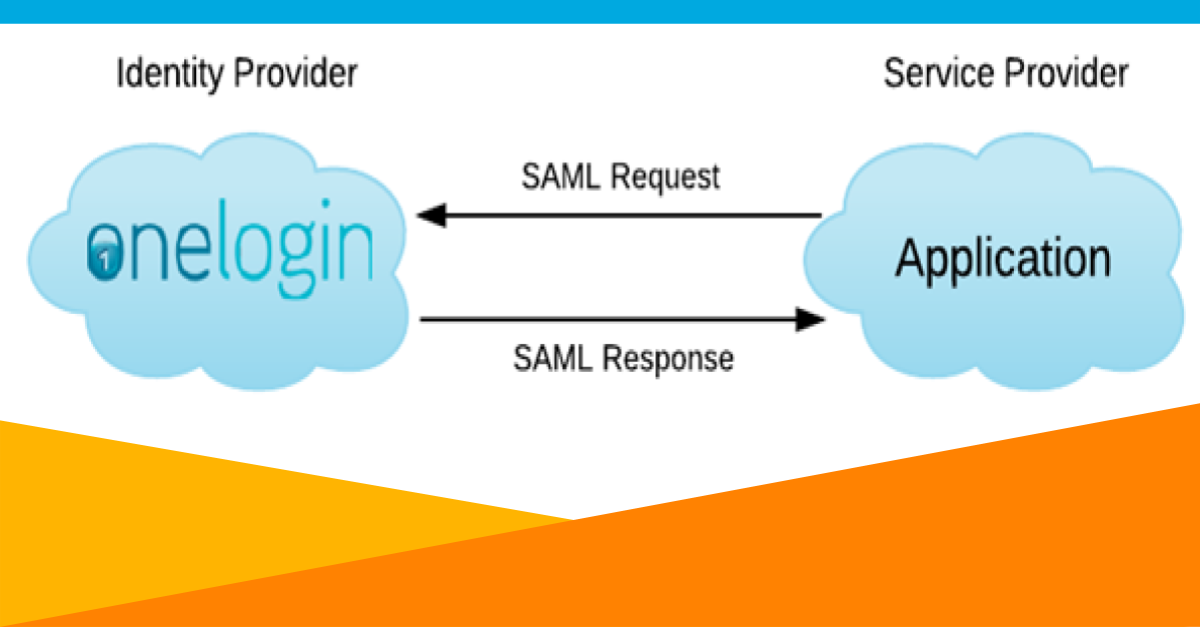
The founder of OneLogin wrote one of our first blogs on SAML in 2012. It’s pretty simple: SAML is a standard that allows OneLogin to securely say “yes, this user is who they say they are” to an application on the user’s behalf. It’s complicated and requires certificates and fingerprints and assertions, but the end user doesn’t care. Those are what you’re paid to care about.
5 Steps to Configuration
Configuring SAML is a heavy lift, but you can make it easier on yourself by doing some prep work. Here are the five most important steps you need to take, ranked in order starting with the most time consuming and ending with the least time consuming.
- Log into your applications as an administrator and gather information
- Sanitize your employee database
- Make choices about security
- Gather the important stuff ahead of time
- Set your colleagues up for success
1. Log into your applications as an administrator and gather information
The most time-consuming task is navigating to each of your vendor’s websites and finding the information you’ll need to enter into the OneLogin admin portal. Depending on the vendor, you might be looking for:
- a login URL
- a logout URL
- a plugin you activate on their website
- the application’s mapping scheme
There may be some other app-specific information your vendor might require, but many software vendors thankfully make the information you need easily accessible. OneLogin’s knowledge base will help you navigate what information you need for each application, as well as where to find it. While there is no way to avoid this initial legwork, a centralized knowledge base makes the information-gathering process simpler.
2. Sanitize your employee database
Ready to have long meetings with internal stakeholders? Because you’ll need buy-in from your organization before you can assign roles and parameters.
When you’re defining Roles for your IAM platform, you’re choosing the buckets your users fall into so you can assign them the correct suite of software. For example, your finance department needs access to different applications than your HR department does, and neither team needs the same access as your sales department.

A Parameter is a piece of data about an employee that you’ll share with a service provider (SP) so they can populate their information fields. The common ones are what you’d expect (email address, first name, last name) but there are some obscure parameters that you might want to pass along, like default language or country code.
Your organization’s employee files (specifically, their roles and parameters) will need to be spotless for OneLogin to share that information with your SPs. As an IT professional, it’s not your job to collect that information, but it will suddenly become your responsibility to fix the problem when bad data means your SAML assertions are rejected.
Hustling beforehand to make sure those ducks are in a row will save you time down the line, so step two is to cleanse and standardize your user data.
3. Make choices about security
This is where you get paid the big bucks. Your job is to define a set of security rules and standards for your organization, document those rules, and enforce them. OneLogin has defined a set of best practices that will help you make these choices.
Consider your organization’s security needs from a broad perspective first. Are your users handling data so sensitive that you want them to change their passwords every thirty days? Should they be required to use Multi-Factor Authentication (MFA) every time their computer goes to sleep? What if they use a personal computer instead of a work-issued computer?
You’ll be working with internal stakeholders to make those decisions. Once you’ve reached a consensus, you can complete step three: decide, document, and distribute your security policies.
4. Gather the important stuff ahead of time
You can save yourself a lot of time during the implementation process by keeping a couple key values on hand. These include:
- your organization’s OneLogin domain, typically [yourdomain].onelogin.com
- your SAML endpoint
- your SHA fingerprint
- your X.509 certificate
Your SAML endpoint, SHA fingerprint, and X.509 certificate are in the SSO tab of any SAML-enabled app in the OneLogin administration view.

Some of these, like your OneLogin domain and X.509 fingerprint, will be used repeatedly during setup processes. It’ll help to have a single repository for them instead of tracking them down each time. Others, like the login URLs, are used in only a couple narrow situations, but are tough to find each time you need them. Step four is having a document to copy-paste from.
5. Set your colleagues up for success
This isn’t necessarily your job, but if you don’t stomp your feet, it won’t get done.
Your organization’s employees are about to be asked to change their habits. A well-designed OneLogin instance will save them time in the future, but they won’t care about that at the moment.
Your people-manager and human resources colleagues will be your partners as you transition people onto the OneLogin platform. When you generate easily-digestible documentation for them to process, you’re saving yourself IT tickets down the road. Give them all the critical information:
- Where do I log in?
- How do I sign up?
- What is my user ID and password?
- What apps do I need to download for MFA?
Once you have those key internal stakeholders on board, you’re done with step five: plan for release.
OneLogin’s identity and access management tools will save you an enormous amount of time in the future if you invest time and resources upfront to configure them properly, and we’re here to support you as you do so. Our knowledge base, customer service team, and guides like the one you’re reading now are your ticket to a smooth transition.