OneLogin welcomes the GDPR as an important and necessary evolution in
the data protection laws across the EU. OneLogin’s privacy and
security program meets and exceeds the highest standards in the industry,
including compliance with the GDPR.
The new General Data Protection
Regulation (“GDPR”), which replaces the
European Commission’s Data Protection Directive, goes into effect on
May 25, 2018. Its goal is to unify European Union (EU) privacy regulations
and better protect EU citizen personal data both within the EU and outside
the EU. As a data processor and controller, OneLogin has verified that we
meet all GDPR requirements and we will continue to actively uphold GDPR
compliance. We are also providing resources and documentation to support
our customers in their roles as data controllers.
At OneLogin, ensuring that all customer data is handled securely and
responsibly is our number one priority. Here is an overview of what to
expect from GDPR, how we are complying with this new regulation, and how
we are empowering customers to comply.
What is the purpose of GDPR?
GDPR is a comprehensive data protection law that serves two purposes:
Protect individual’s data: GDPR gives control
over personal data back to the EU residents and prohibits organizations
from exploiting that data.
Guidelines for Organizations: GDPR makes data
protection law identical throughout the single market. It provides
businesses with simpler legal guidelines, which can be more easily
enforced by government bodies.
Who does GDPR apply to?
GDPR applies to any organization operating within the EU, as
well as organizations that offer goods or services to customers or
businesses in the EU. This broadens the scope of protection of
EU residents for improved privacy control.
How will GDPR affect me?
If you are a resident of the EU, congratulations! The European Union is
taking steps to ensure that your data is used safely and appropriately.
If your organization provides services within the EU, you will need to
be compliant with GDPR. This will impact the way that you store, process,
and utilize user data in a number of ways. See this overview of key
changes introduced by GDPR as it replaces the European Commission’s
Data Protection Directive.
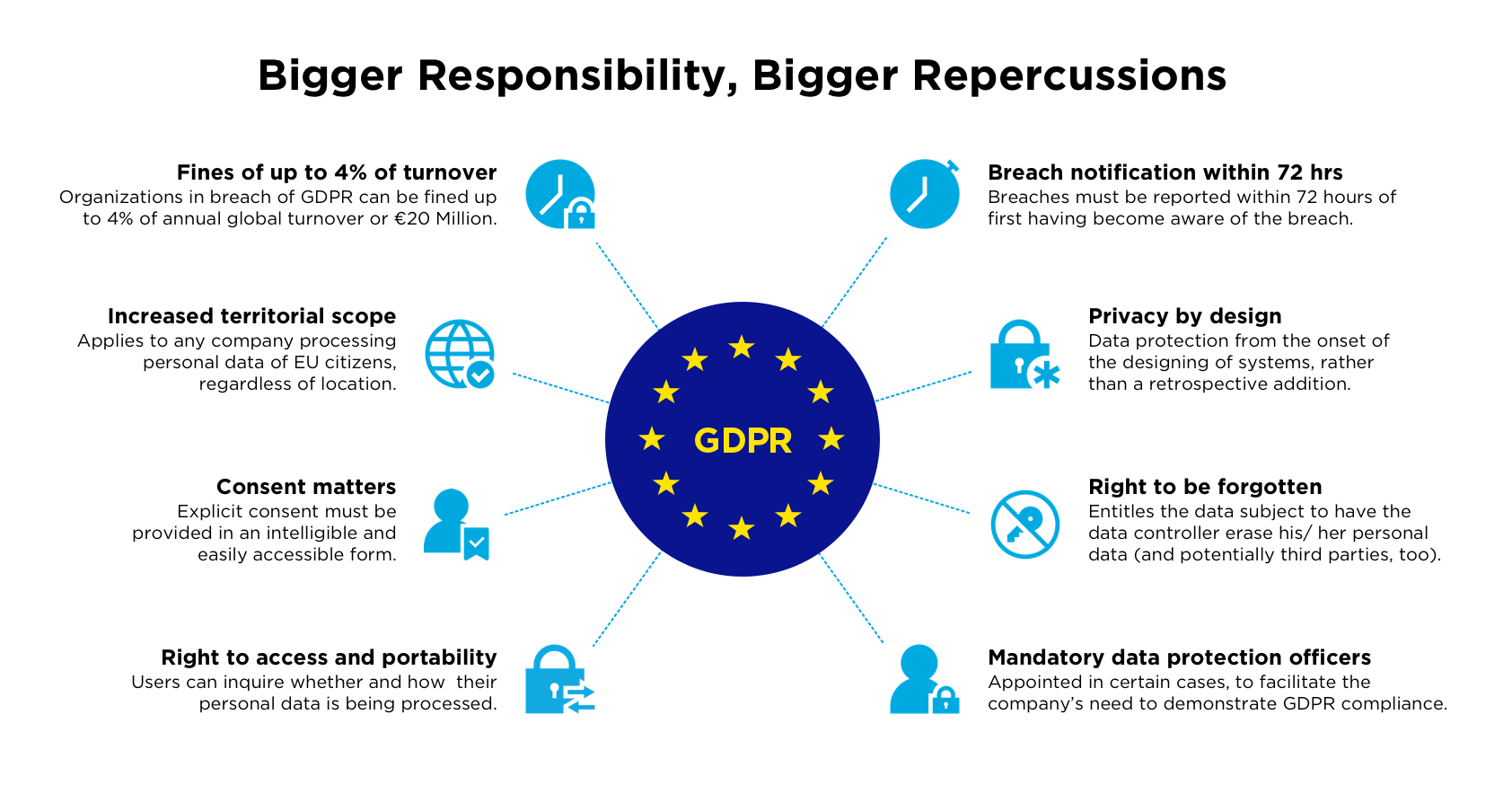
Right to access and portability: Users can request
confirmation as to whether their personal data is being processed, where
and for what purpose. Further, the data controller is required to provide
a copy of the personal data, free of charge, in an electronic format.
Breach notification requirement: Breaches, which are
likely to “result in a risk for the rights and freedoms of
individuals”, must be reported within 72 hours of first having
become aware of the breach.
Privacy by design:Companies must take into account data
privacy during design stages of all projects along with the lifecycle of
the relevant data process. Companies must also take into account data
privacy during design stages of all projects along with the lifecycle of
the relevant data process.
Right to be forgotten: Companies must allow users to
erase their personal data, cease further dissemination of the data, and
potentially have third parties halt processing of the data.
This is not an exhaustive list. But fail to meet any of these
requirements, and you may be fined up to 4% of your annual growth
turnover, or €20 million.
What steps is OneLogin taking to be GDPR compliant?
OneLogin is a global organization that both processes and controls data
from around the world, including the EU. Our existing certifications and
long-standing commitment to privacy frameworks prepare us for GDPR in many
ways.
To meet GDPR requirements, organizations are required to articulate
data flows, and demonstrate how privacy is controlled and maintained.
Our “Blank Page” approach to redrawing our
data flows and building out very detailed data mapping diagrams helps us
to achieve this.
Updated Standard MSA and Data Processing Agreement:
Organizations are also required to update their contractual language to
reflect the additional accountability required by GDPR. To this end,
OneLogin leverages data breach notification language, uses
subcontractors, and communicates responsibilities to our own data
processing vendors.
Data Protection Officer: OneLogin utilizes an
independent external consultant based in the EU to serve as our DPO.
How is OneLogin helping customers to be compliant?
OneLogin is dedicated to empowering customers with the resources they
need to comply with GDPR. Here’s how:
Right to access and portability
- IT administrators can easily find a user in the system and print out
their information as stored in any of the user directories.
- User privileges and role assignments in OneLogin indicate where the
user’s metadata is used (i.e. all applications they have access
to.)
Breach notification requirement
- OneLogin’s event streaming service can help identify breach
attempts much faster when correlated with additional enterprise security
events.
- Following the identification of a potential breach, administrators can
use OneLogin’s event dashboard and reporting tool in order to
investigate further.
Right to be forgotten
- OneLogin allows for the automated deprovisioning of users from other
systems and external applications.
- Admins can delete users immediately to meet both privacy and
enterprise security requirements.
- Admins can also manually audit provisioned apps.
Privacy by design: OneLogin is a trusted partner
Privacy
by design is a particularly challenging requirement, but as a vendor we
are well-prepared for it.
- The OneLogin service has always handled information that must be
protected; whether due to privacy regulations, credit card industry
regulation, its designation as shared secrets, or several other data
protection requirements.
- OneLogin incorporates privacy impact assessments that are performed
periodically and as part of the design process for new features.
Privacy by design: A better architecture with OneLogin
Especially
if you are an architect in IT or engineering, you might be thinking not
only about your third parties’ compliance, but the compliance
challenges in your own systems. Consider the advantages of building your
integrations on top of OneLogin’s platform.
Many of the compliance challenges are the result of older architectures
that allow for limited control over how data is stored, managed, and
processed. For example, it used to be very common for legacy applications
to access the corporate directory directly. This meant they typically had
access to all user information with few restrictions on what they modify,
cache or store.
We have come a long way since.
To understand how, let’s start with some essentials. The core of
OneLogin’s identity platform is modern protocols, including SAML,
OpenID
Connect
and SCIM.
These modern
protocols use secure tokens, security assertions and automated
provisioning.
- Secure tokens: The user never signs-in to an app
directly. Instead, the user always signs-in securely using a Single
Sign-On (SSO) portal. Any trusted app can receive a secure
token
that represents the user.
- Security assertions: Identity information (e.g. user
name, employee ID) is digitally signed by a trusted party, specifically
an identity provider.
- Automated provisioning/deprovisioning: When a user is
granted access to an application, their relevant metadata is pushed to
the app. Similarly, when a user’s access is revoked, their relevant
metadata is deleted from the app.
OneLogin’s Identity Platform enables you to leverage modern
protocols for virtually any public cloud or private/custom app.
Advantages:
- Applications do not authenticate users directly, which means better
security and privacy.
- Applications do not have direct access to the corporate directory for
read/write to the entire user base.
- Applications get only the user metadata they need — only for
users with access to the app, and user’s access can even be
anonymous.
- Applications can get role/privilege information without direct access
to the user’s information.
You can learn more about how we are embracing GDPR by reviewing our
privacy policy.
If you have questions or need more information please email privacy@onelogin.com.






