Set Password Security for a Policy
OneLogin provides a variety of settings for managing passwords. Your available settings depend on the plan you've chosen. If you are using the 30-day free trial, by default users are assigned the Default policy and you can change password security for all users by changing the settings for that policy. This procedure assumes you are changing the default policy.
Log in to your OneLogin account owner account.
Click Administration on the toolbar to go to the Admin panel.
Go to Security > Policies.
Click OneLogin Protect.
Use the tabs to change the security settings for all users assigned this policy. In the 30-day free trial, by default, all new users are assigned this policy, so all existing and new users will be affected.
- Sign In tab lets you control how passwords behave for the policy.
- Session tab lets you control session login, lockout, and inactivity behavior.
- MFA tab provides options for any multi-factor authentication (MFA) associated with the policy. Note that MFA is available in the 30-day-free-trial, Enterprise, and Unlimited plans.
- IP Addresses tab lets you enter a Allow List of IP addresses, denying login attempts from locations other than those addresses.
- Customization tab lets you enter a system use notification. You can choose to display the notification before every login attempt.
See the sections below for details on the settings in each tab.
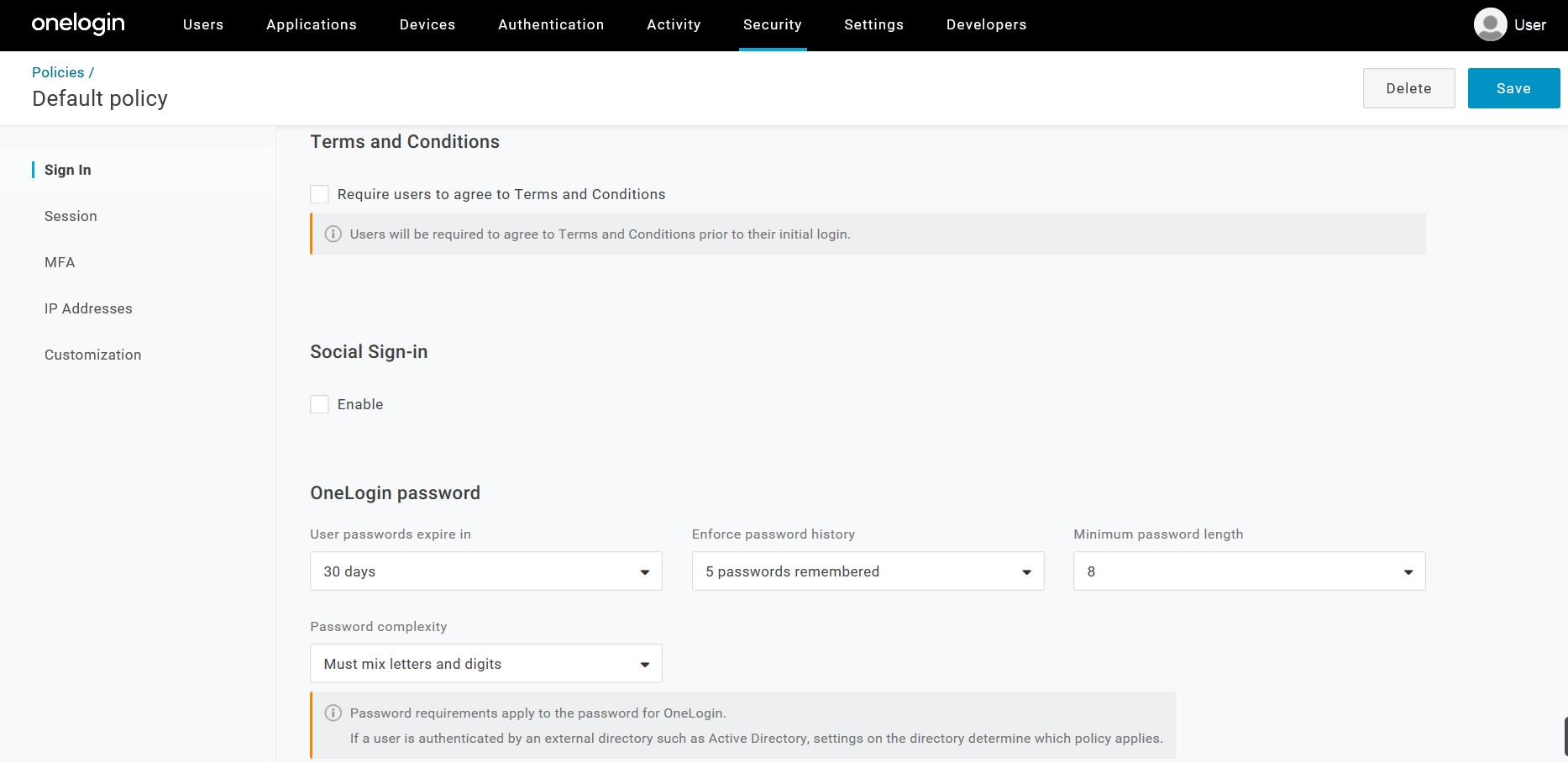
Sign in Tab
Terms and Conditions
Select whether new users must agree to your terms and conditions upon initial login.
Social Sign-In
Select which social media sites you want to disable MFA for by using Enable and choosing the sites you want.
OneLogin password
Use User passwords expire in to define the amount of time that a user's password remains valid before it must be changed.
Use Enforce password history to define the amount of time a user's old password stays in the system and cannot be re-used again.
Use Minimum password length to define the minimum required length of a user's password.
Use Password complexity to define the level of complexity that a password must have from letters, numbers, capital letters, and special characters.
Browser Extension
Use Allow users to install browser extensions from their Profile page to allow users to download browser extensions from their Profile page.
Use Users can add Company apps and Users can add Personal apps to allow them to add apps to their personal apps or company apps list on their portal or browser extension app drop-down.
Auto suspend inactive users
Use Users that have not signed-in for 90 days will be automatically suspended to suspend inactive users from accessing OneLogin.
Password Update
Use Redirect users to external site when resetting password, for example if you are using a third-party service to handle password resets.
Use Allow Users to Update their Directory Password to enable users to update their password in OneLogin. This will give them a "Forgot Password?" link on their login page. This option must be enabled for users to receive invitations to OneLogin with a link to set their own password.
Note. Later, if you choose to have users use a third-party directory (Active Directory, LDAP, G Suite) password for OneLogin authentication, you will want to disable this option.
Use Resetting password unlocks user account to ensure that when users reset their password it will also force their accounts to unlock, if they had been locked before.
Password reset redirect
Use Redirect users to external site when resetting password to redirect users to a password reset URL when they initiate a password reset.
You have the option of including a confirmation message that they will see before they get redirected to the password reset URL.
Session Tab
Login Attempts
Use Maximum invalid login attempts to define the number of times a user can fail to input incorrect login credentials before they are locked out of their account.
Set the Lock effective period to the period of time that a user's lockout period should last.
Timeout
Use Timeout should occur based on to select whether the user's session should timeout after a set period of Time (user must reauthenticate with OneLogin after 2 hours, for example, whether the user is active or not) or after a set period of Inactivity (user must reauthenticate with OneLogin after 2 hours of inactivity, for example). Select the amount of time from the Time Period dropdown.
You can also specify that users see a Keep me signed in option on their login screen.
MFA Tab
Note that MFA is available in the 30-day free trial, Enterprise and Unlimited plans. In the Starter plan, authentication factors are not available. To use MFA in the Starter plan, upgrade and then request MFA as an add-on through the support form in OneLogin.
MFA Tab
Require trusted device
Define the PKI certificates to be used for a second authentication factor. Use Enabled to require users to use MFA. Use Allow self-installation to enable users who require certificates to be prompted to install a certificate after they authenticate, but before they can sign into any applications. You can set the certificate to expire in 1, 2, or 5 years.
One-time passwords
Use OTP Auth Required to require users to enter a password. Use one of the Available factors to authenticate users.
Phone number for SMS
Use Allow user to change phone number for OneLogin SMS to allow users to change the phone number used for SMS verification from their profile. (Note that a directory mapping will overwrite a user-entered phone number.)
MFA device registration
Use Users without an MFA device must register one before being able to login OR
Use Do not prompt users to register an MFA device during login. Note that all users who have this policy assigned to them will have access to MFA from their profile page.
MFA bypass
Enter any Allow Listed IP addresses, so that the policy will not be applied to anyone logging in from a listed address.
Note. This serves a different purpose from the Approved IP addresses field on the IP Addresses tab. Allow Listing an IP address here causes the MFA policy you create to be bypassed when users log in from a listed IP address. However, entering addresses in the Allowed IP addresses on the IP Addresses tab requires users to be restricted to logging in only from the addresses listed in the Allowed IP addresses field, regardless of any MFA methods, such as OneLogin one time password.
Use Ignore X-Forwarded-For header IP address to have OneLogin evaluate only the gateway IP address and ignore the IP addresses from the X-Forwarded-For header.
Enforcement settings
Use OTP required for to set enforcement settings. Choose from Administrator only, Configured users only, or All users. Use OTP required at to determine At every login or Unknown Browser. You can also set the number of days you want to set Security cookie expiration.
Note: In addition to OneLogin’s free one-time password (OTP) app, OneLogin comes pre-integrated with Duo Security, RSA SecurID and many others.
IP Address Tab
IP Address Tab
IP address allow list
Enter IP addresses to deny login attempts from locations other than those addresses.
Customization Tab
IP Address Tab
System Use Notification
Enter a system use notification. Use Show system use notification before every login to display the notification before every login attempt.
If you’ve been using OneLogin’s free 30-day trial, click here to learn how to buy OneLogin.
