
What to look for in Multi-factor Authentication
OneLogin Protect recently graduated into general availability, and I’m incredibly pleased. Using it has made it easier for me to access my applications securely and faster than ever before.
So what is OneLogin Protect?
OneLogin Protect is a rethink of what Multi-factor Authentication should be. It’s the MFA we’ve always wanted to use ourselves. Because, like you, we’ve had to deal with clunky multifactor authentication methods for too long during our careers.
The Pain of MFA
First, there were the RSA key fobs that required you to have to hunt down the fob somewhere deep in your laptop bag, hoping you hadn’t lost the little bugger. Then manually type in a code — correctly, before it expired — into your computer.

Beyond being annoying, these were an insidious drain on company productivity. The whole process took roughly a minute, halting whatever you were working on and interrupting your train of thought. Studies show that interruptions like this can degrade productivity for up to 25 minutes. And when you were interrupted multiple times a day to enter a code, the problem only got worse.
Even worse, users often complained to IT about having to enter codes so often. This put IT into a bind. Either reduce MFA frequency and degrade security by relying on weak password-only authentication. Or, maintain MFA frequency and keep the complaints coming.
Later, companies started putting MFA into a mobile phone app. This eliminated the “dig through the laptop bag” problem since you typically keep our phone close at hand. But it introduced a different kind of digging: finding the MFA phone app among the dozens of other apps on your phone.
Even worse, what if you have multiple MFA apps have “Auth” in their name? Good luck finding the right one.

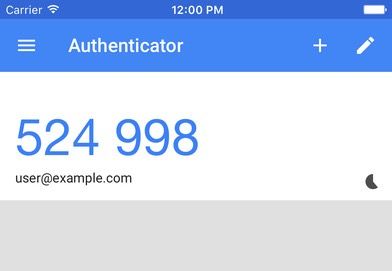
These “software token” mobile apps still required you to manually transcribe the code — correctly, in a stressfully short time window — into your laptop. Here’s Google Authenticator, for example:
How we’re fixing MFA
Given these clunky alternatives, we asked ourselves, How can we do better? How can we stop this constant, annoying productivity drain?
It came down to the following goals:
- Reduce the number of interruptions.
- Reduce the duration of each interruption.
We addressed the first goal — interruption frequency — when we released Adaptive Authentication back in March, so that users are only prompted for MFA when there’s an actual risk. So that left interruption duration as the problem to tackle, which meant we had to do the following:
- Run on a device the user always had close at hand, like their phone — or watch
- Eliminate the “hunt for the app” problem
- Eliminate the “enter the code” problem
We’re thrilled to say that we’ve solved these problems with OneLogin Protect. Here’s how it works.
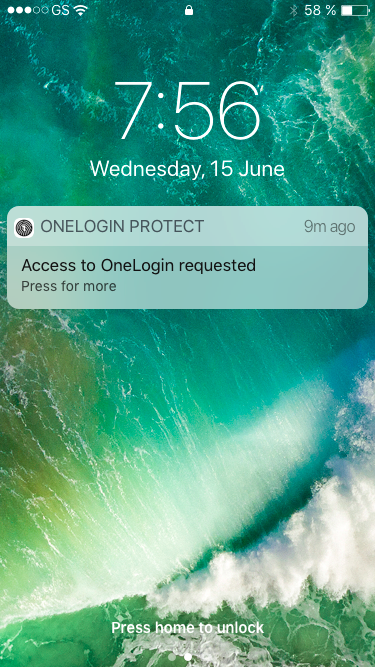
Let’s say your phone is locked. You MFA access request appears on your lock screen as a notification like this. (iOS is on the left, with Android on the right.) No more hunting for your MFA app!
You tap on the notification, then are prompted to Accept or Deny the request. No more codes to enter!
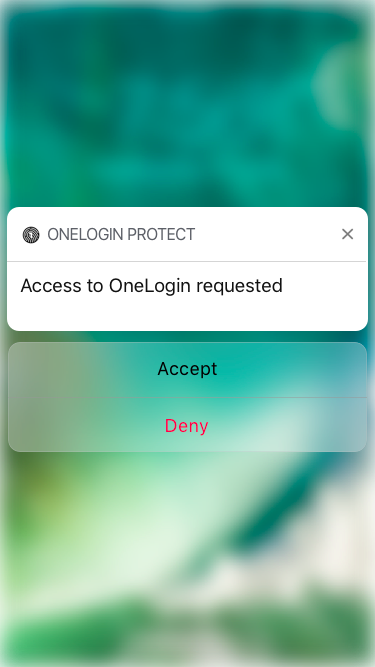
For security, we need to ensure that someone hasn’t stolen your phone and is using it to accept fraudulent MFA requests, so we prompt you to use your touch ID to unlock your phone, and you’re done!
It’s even easier if your phone is not currently locked. You just accept the notification, and you’re done.
No digging through laptop bags or screens of mobile apps.
No entering a code before it expires.
What previously took a minute now takes seconds.
But we didn’t stop there. We wanted to see if we could shave that down even further. So we made it so that, if you had an Apple Watch or Android Wear watch paired with your phone, the notification alerts would appear on your phone. In this case, all you have to do is tap Accept on your watch, and you’re done!
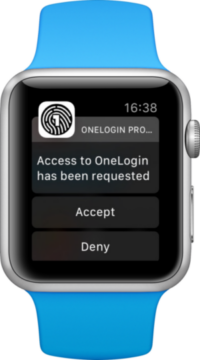
This took the MFA process down to the time it takes for you to tap a button your watch, or about two seconds.
So, we’ve reduced a one minute interrupt down to a couple of seconds. This is one of the most important things to look for in multifactor authentication, since it means employees stay in the flow of their work, are happier with IT, and more productive. At the same time, there’s still an additional factor in the authentication process, your phone or watch.
Keeping MFA secure
Now, how do we ensure that the OneLogin Protect mobile application itself is a secure authentication method?
First, on your phone, download the OneLogin Protect mobile app on the Apple Store or Android Play.
Then, on your laptop’s browser, visit the OneLogin single sign-on portal, typically at yourcompany.onelogin.com. If your OneLogin administrator has turned on two-factor authentication, you’ll see a login screen like this:
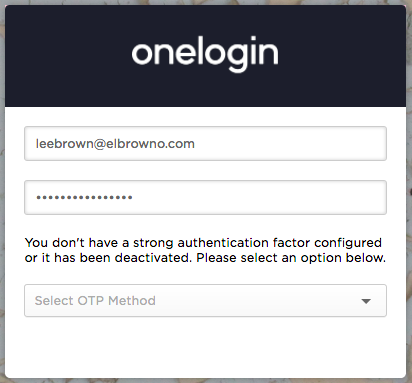
Log in with your OneLogin username and password. Then select OneLogin Protect as your strong authentication factor. (This is because OneLogin supports other authentication factors, including MFA applications such as Duo, and hardware tokens such as Yubikey.)
To help configure your OneLogin Protect app, you’ll then see a QR code like this on your browser:
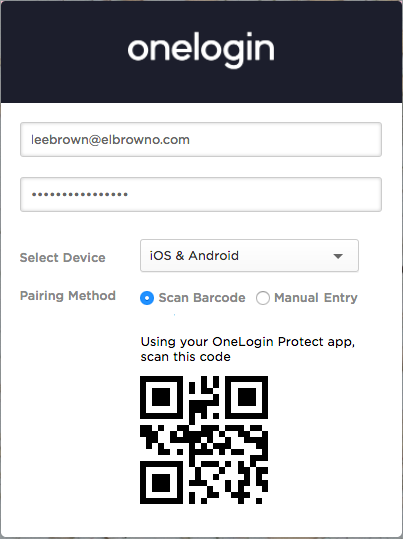
Go back to your phone, and scan the code using the OneLogin Protect app. You’ll see a screen like this:

Make sure that OneLogin Protect can send push notifications, and you’re good to go. Your instance of OneLogin Protect is securely bound to your OneLogin account. You can exit OneLogin Protect. Next time you’re prompted for MFA, you’ll see a notification similar to this:
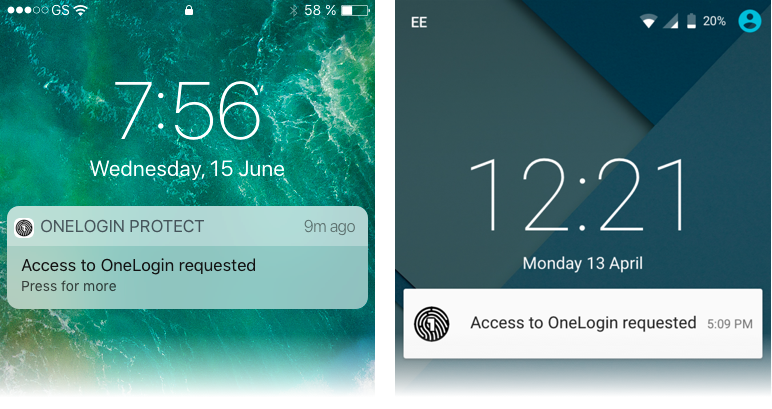
… which will kick off the workflow described at the start of this post.
To sum up, this is what to look for in MFA in plain English: the ability to securely authenticate into applications in seconds, not minutes, using certified phones, while ensuring that stolen phones cannot be used to fraudulently MFA. We call this Minimally Intrusive MFA — and it’s important to look for, since not all MFA is created equal.
But we’re not stopping here. We’re working on a number of other MFA features that make OneLogin Protect even better. So stay tuned.
In the meantime, you can learn more about OneLogin Protect in our documentation and download the OneLogin Protect iOS application or Android application.

