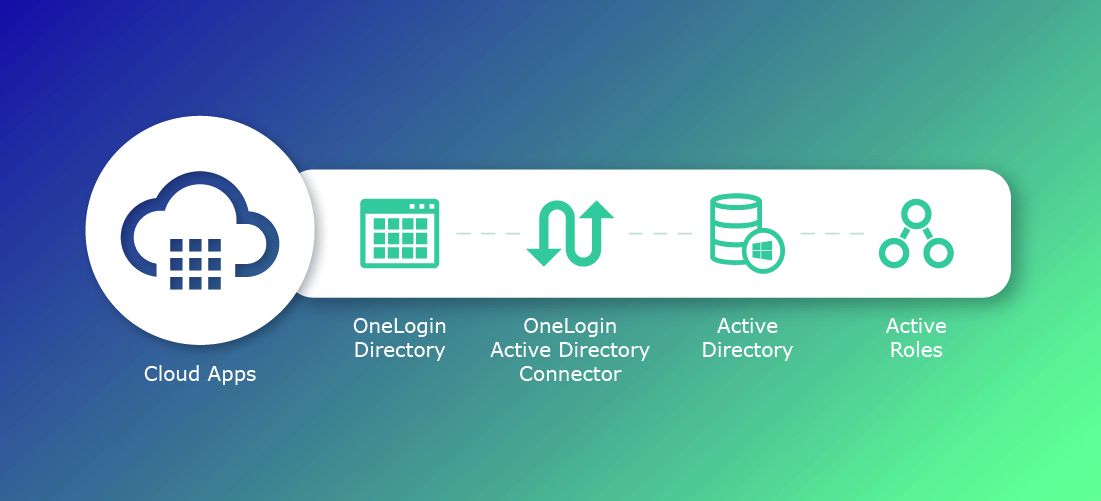
OneLogin has provided automatic provisioning for years. With provisioning, you can automatically assign users to applications based upon their user attributes, and you can automatically assign them application entitlements based upon those same attributes. For example, a new employee may be a new manager in the Marketing department. Because they are part of the Marketing department OneLogin could automatically assign them to a role that assigns them to Marketo. At the same time, given their title as “Manager,” OneLogin ensures they have an account in Marketo that has access to all campaigns. So, from day one, employees such as this Marketing Manager can log in to the applications they need to do their job. This can work perfectly if the attributes are accurate and kept up to date.
The problem comes when those attributes are not accurate or kept up to date. Inaccuracies can occur because of simple human error, lack of resources, miscommunications, etc. If this is the case, you need a way to empower application admins and/or managers to control who has access to what in an easy and secure manner. If OneLogin is your main user directory, you can assign app admins and managers Role Admin privileges within OneLogin and give them the ability to add or remove users from OneLogin roles. OneLogin Roles are usually used to assign users to one or more applications, thus add or remove users from a role assigns them to or unassigns them from the applications associated with those roles.
Now, what if you are using Active Directory (AD) and OneLogin? Then you are faced with managing roles in OneLogin and Windows Security Groups in Active Directory. If you have ever tried to delegate control to AD users to manage membership in particular Windows Security Groups, it can become quite tedious, and you are still presenting your users with two different interfaces to manage these memberships: OneLogin and Active Directory.
How do you solve this problem? By using One Identity Active Roles! Active Roles gives you an effortless way to delegate control over Active Directory objects and a simple interface for your users to use to manage the exact tasks we have been discussing – managing membership of Windows Security Groups. You can then use these groups within OneLogin to automatically assign users to roles and thus their related applications without having to worry about creating Role admins and force your users to use two separate interfaces to manage access to resources. In our Marketing Manager example, we can automatically assign our new employee to the Marketo role in OneLogin based upon the fact that they belong to a Windows group called “Marketing Managers” and the Marketing Director could be the one to assign them to the Windows group.
So, how does this all work?
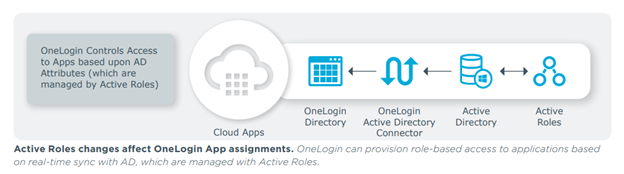
Users such as application owners or managers are granted the ability to manage the membership of groups that are relevant to them. These group memberships are stored in Active Directory. Active Directory syncs users with OneLogin through the OneLogin Active Directory Connector. OneLogin then contains Mappings that assign users to particular OneLogin Roles and thus to specific apps based upon the users belonging to a given Windows group.
Let’s take a simple example and walk through it
Our sample company, OneLo Gin Distillery, is currently using Active Directory to manage on-prem objects and access to on-prem resources.
They need to roll out Salesforce to their sales team. They know they want to use OneLogin to log in to Salesforce. They plan to use the OneLogin Active Directory Connector to synchronize users with OneLogin and give users the ability to log in to the OneLogin portal with their Active Directory credentials.
They would also like to empower their Sales Manager to easily control who has access to Salesforce as well as other resources that are needed by those on the Sales team.
In OneLogin:
- Install and Configure the Active Directory Connector
- Add in App Connectors
- Create a Role to Assign to the App Connectors
- Create a Mapping to Assign Users to the Role based upon Windows Group membership
In Active Roles:
As a Manager:
- Use Active Roles to Assign a user to a Windows Group
In OneLogin
Install and Configure the Active Directory Connector
Installing and configuring the Active Directory Connector (ADC) is straightforward. You can directly download the connector software from the OneLogin Admin UI and follow the instructions given.
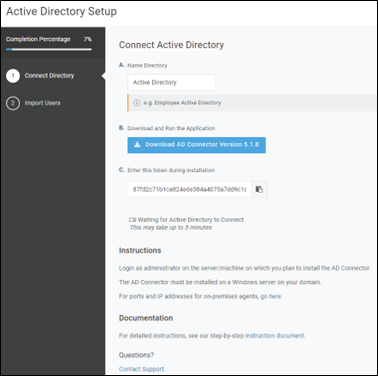
Figure 1– Active Directory Connector Setup Wizard
Once the ADC is installed you can then sync your AD users with OneLogin. All their attributes, including the Windows Security Groups they belong to, will then be replicated into OneLogin.
Add in App Connectors
Once you have ensured that your users can log in to OneLogin securely you can start adding in your app connectors. In this case, our company, Onelo Gin Distillery, is looking to add Salesforce.
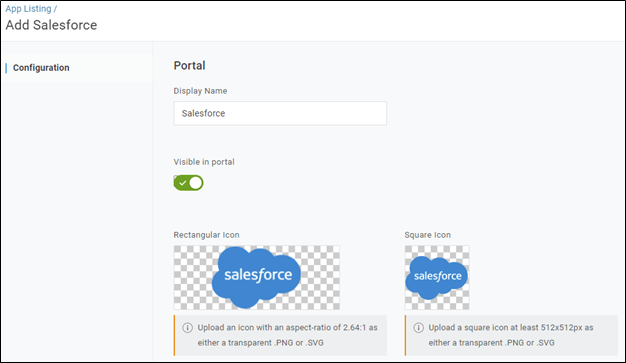
Figure 2 – Salesforce App Connector
The OneLogin Salesforce App Connector supports both provisioning (the ability to create user accounts within the application itself) and single sign-on, SSO, (the ability to log in securely from OneLogin). We recommend that if your license supports provisioning that you configure provisioning before you configure SSO.
Create a Role to Assign to the App Connectors
Once you have configured an app connector you can directly assign it to users, but it is much easier to control access through OneLogin Roles. A OneLogin Role can be associated with one or more app connectors and then assigned to users directly or automatically based upon a user matching certain attributes, such as belonging to a particular Windows Security Group.
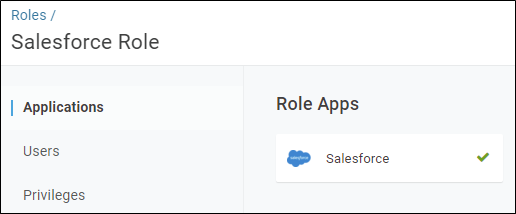
Figure 3 – OneLogin Role
Create a Mapping to Assign Users to the Role based upon Windows Group membership
Once you have your users, your app connectors and roles defined you can then use Mappings to automatically assign users to the necessary roles. In this case, our OneLo Gin Distillery admin would want to Assign users that belong to the “Sales – Salesforce” Windows Group to the OneLogin Salesforce Role.
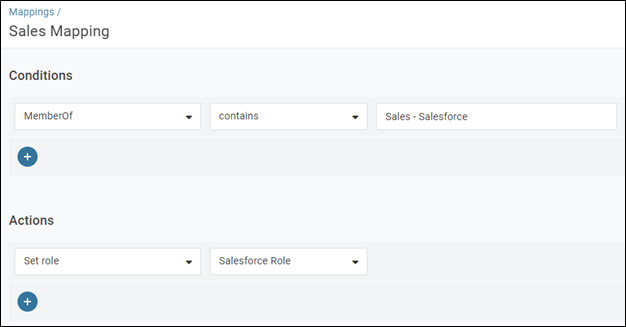
Figure 4 – OneLogin Mapping
In Active Roles
At this point we could simply work with Active Directory and delegate the ability to manage, but this could be a bit confusing and our Sales Manager would need Active Directory tools installed on their desktop. Active Roles can make this process much easier.
At minimum, you need to create an Access Template, which defines the types of permissions you want to grant; a Managed Unit, which defines which objects you want to grant control over and then simply delegate the permissions based upon the Access Template you have created over the Manage Unit.
Create an Access Template
Access templates are key to making control delegation within Active Directory easier. Active Roles comes with several dozen out-of-the-box Access Templates that contain the permissions needed to perform common administrative tasks such as “Adding/Removing users from a group”. Thus, you can simply copy these existing templates and use them for your own purposes.
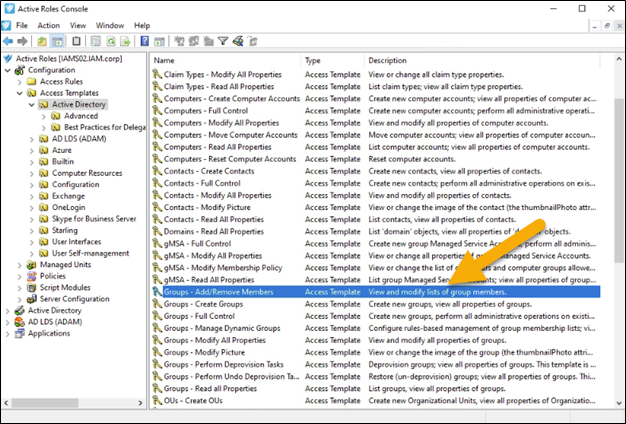
Figure 5 – Active Roles Console with OOB (out of the box) Access Templates
As you can see there are quite a few permissions needed if a user is going to be adding/removing members from a group.
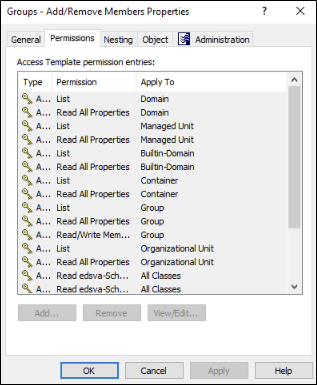
Figure 6 – Permissions needed to Add/Remove Group Members
Thus, it is easier to start with a pre-defined Access Template, copy it and then modify it as necessary. For this particular use case you can simply copy the existing “Groups – Add/Remove Members Properties” and save it under a unique name.
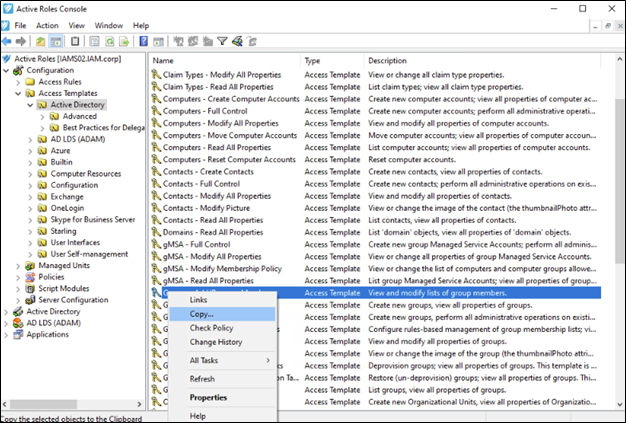
Figure 7 – Copy OOB Access Template
Create a Managed Unit
Once you have created the necessary Access Template, you will need to define a Managed Unit so you can limit your user to only managing certain groups. In this case, Onelo Gin Distillery will want to limit the Sales Manager to only managing security groups that begin with the word “Sales.” In this case we currently have two groups that begin with the word “Sales.”
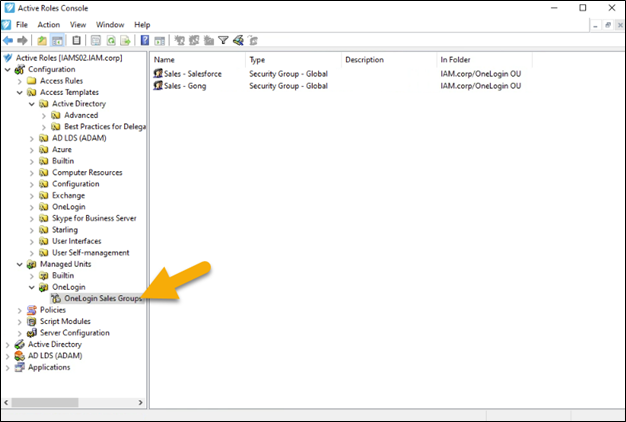
Figure 8 – OneLogin Sales Group Managed Unit
The objects that are part of a Managed Unit can be explicitly defined or based upon a query.
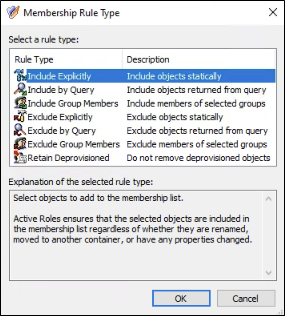
Figure 9 – Managed Unit Membership Rule Type Options
In this case, our admin has created a Managed Unit based upon an “Include by Query” rule. The rule is looking for all groups within the IAM.corp domain that have “Sales” in the name.
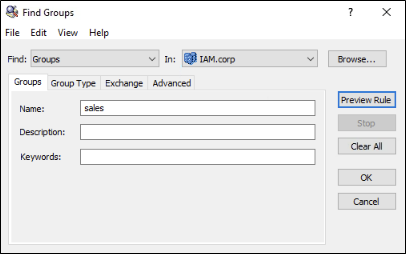
Figure 10 – Membership Rule for OneLogin Sales Managed Unit
Delegate Control
The final step in Active Roles is to delegate control of the Managed Unit (OneLogin Sales Groups) you have defined to a particular user (our Sales Manager, Martin Yee) using a particular Access Template (OneLogin Group Management).
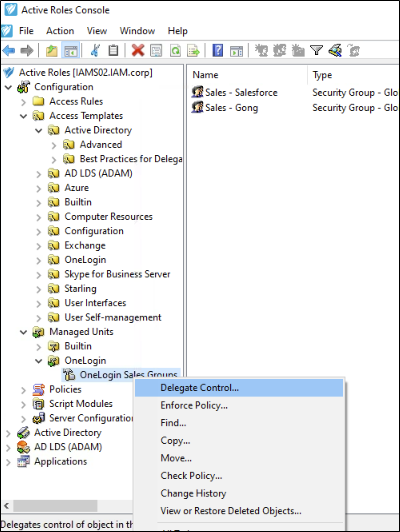
Figure 11 – Right Click on Managed Unit and Select Delegate Control
Choose the user or group you want to delegate control to.
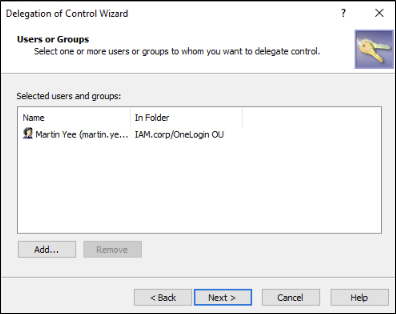
Figure 12 – Choose Martin Yee to Delegate Control To
Choose the appropriate Access Template.
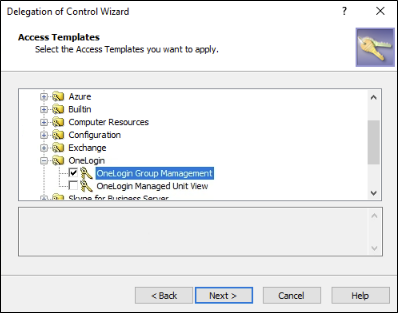
Figure 13 – Choose the OneLogin Group Management Access Template
And complete the Wizard.
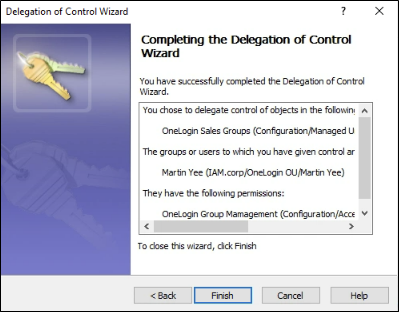
Figure 14 – Completion of Delegation of Control Wizard
As a Manager
Now our manager, Martin Yee, can log in to the Active Roles Web UI and add users to the Sales – Salesforce windows group.
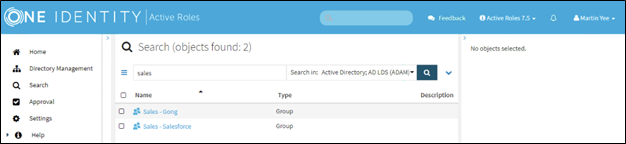
Figure 15 – Martin Yee logged into ARWebAdmin
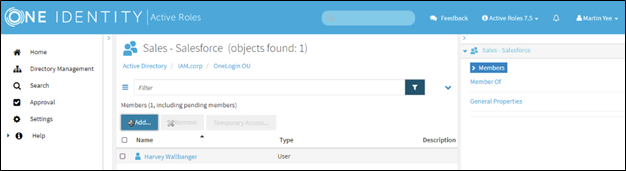
Figure 16 – User added to group by Martin Yee
You could now look at the user in OneLogin and see which Windows groups they are a member of.
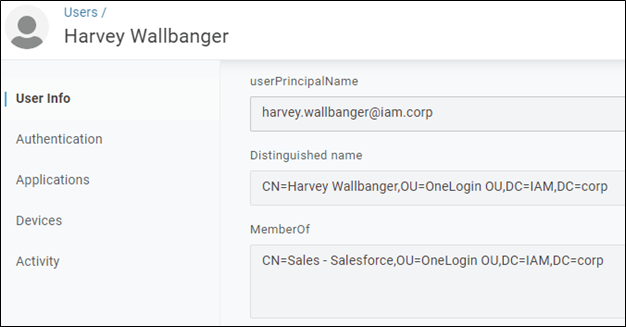
Figure 17 – Harvey’s User Record
And finally, when our new employee, Harvey Wallbanger, logs in to OneLogin they will see a tile for Salesforce.
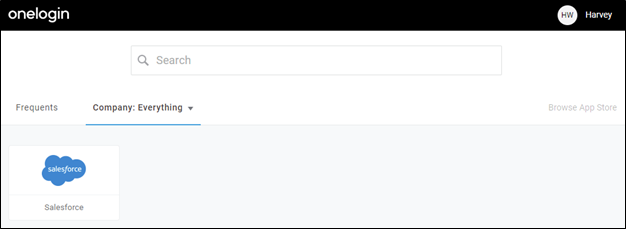
Figure 18 – Harvey sees Salesforce Tile
Conclusion
A lot of today’s technology has automation capabilities built in. Unfortunately, much of this automation is dependent on the data that it is looking at being accurate and up to date. The reality is that this data, for whatever reason, is not always accurate and up to date. When this occurs, IT often must step in and manually take things over. This puts an extra burden on your IT staff. The solution we have presented here: empowering users to control who in their team has access to resources on their own takes the burden off the IT team while still ensuring that users get access to the resources they need in a timely and secure manner. One Identity Active Roles, Active Directory and OneLogin work seamlessly together to provide users with access to resources both on-premises and in the cloud.
Learn more by viewing OneLogin and One Identity Active Roles unlocking the value of this powerful combination.

