“Those who sacrifice liberty for the sake of security deserve neither.”
You’ve heard that directionally in-tune but not-quite-accurate paraphrase of Benjamin Franklin – probably in the context of having to take your shoes off at the airport or concerns over allegedly expansive government surveillance programs.
While I’m willing to bet my bifocals Benjy wasn’t thinking about cybersecurity products when he said something kinda-sorta like that, I think about that sentiment – the idea that your experience and security have been at odds with one another – all the time in the context of cybersecurity.
You Know the Drill
We’ve all seen the movie before. You can access corporate apps from your couch … but you’ve got to be on the VPN. We’ll issue you a phone … but there’ll be an MDM agent on it. We’ll let you access the web… but we’re going to URL filter the heck out of it and prevent you from accessing the sites you want.
It kind of makes sense: sometimes you have to sacrifice a little usability for the sake of security. I mean, you don’t want to be the one to take down your company because you clicked on the wrong link, right?
There’s Got to Be a Better Way!
But what so many folks take for granted today (or are completely unaware of) is the new mentality around security and usability that has emerged and matured over the last decade or so – and a new class of technologies to support it.
Who remembers Whack-a-Mole? If you make the secure thing the hard thing, users won’t do the secure thing, and you’ve created a Whack-a-Mole scenario where you’re chasing ghosts. And they’re not evil – they’re just trying to get their jobs done.
It’s too easy for users to spin up their own apps, use their personal devices – even their personal credentials. Poof. Ghost mode. Good luck securing that. To succeed in 2018, you have to make the secure thing the easy thing.
This means your security program – from your mentality to your strategy to your vendor selection process – needs to account for the end-user experience every step of the way, or risk circumvention. Time for a simple two-by-two.
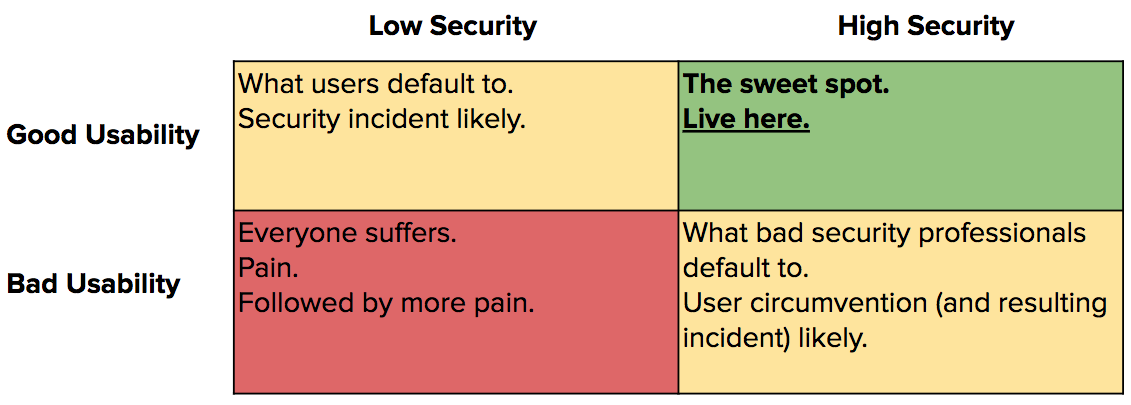
I don’t like tables. Can you give me an example?
Sure. When I worked in the Cloud Access Security Broker (CASB) space, a hot topic of conversation was whether the API-based approach – where CASBs integrated directly with SaaS apps for DLP and UEBA purposes – was superior to the proxy-based approach – where CASBs operated by brokering traffic in-line.
The knock against the API-based approach? It was incapable of blocking the input of sensitive data into cloud apps because it was reactive (even if “reactive” meant removing or encrypting the data seconds later).
The knock against the proxy-based approach? It negatively impacted the user experience (slowed things down, broke search, struggled to deal with encrypted data).
The other problem with the proxy-based approach? Because it was limited to in-band traffic, users could hop on a personal device and avoid the proxy – and they were motivated to, because proxies can be tough. The secure thing was the hard thing, so users circumvented it. And now you’re back at square one.
Got it. Usability & Security = Peanut Butter & Jelly. Now what?
The most successful security leaders we’ve seen observe a handful of best practices.
- Build usability into your security program charter. Hire for it, incentivize it, reward for it. Remember the two-by-two.
- Bake it into vendor selection process and ask vendors how their offering supports a better usability = better security approach.
- Partner with your users. Security is everyone’s responsibility. Listen to them, educate them, train them (and not just with the corny eLearning modules). Be creative! Our CSO Justin Calmus has led super fascinating and informative internal sessions on hacking and got everyone to put their black hats on.
How OneLogin Balances Usability & Security
It’s not enough to talk the talk. We need to walk the walk. From a product standpoint…
- Secure Single Sign-On Portal. Sure, the OneLogin admin can enforce a rigorous password policy to access the SSO portal – but once you enter it, you have immediate access to all of your apps! I’m never going back to the days of sticky notes and/or spreadsheets to keep track of URLs / usernames / passwords. Which is good, because that is not secure.
- Adaptive Multi-Factor Authentication powered by machine-learning. Something unusual happening? Let’s step up authentication. Working from home on the same machine with the same OS and the same browser version and a successful password entry for the seventeenth Friday in a row? Maybe we should trust you.
- OneLogin Protect. Our one-time-password (OTP) app makes life way easier. Don’t take my word for it. Check out this in-depth product breakdown by our Senior Director for Mobile products and initiatives, Jeff Broberg
We could go on, but what I find more interesting are the developments our customers are making in this area. More on bending the security-vs-usability spectrum soon.
How are you balancing usability and security? Let us know.